Security At Events

With a large amount of people gathered at events security issues can arise in many forms from terrorist threats and protests to mishaps in equipment and general emergencies.
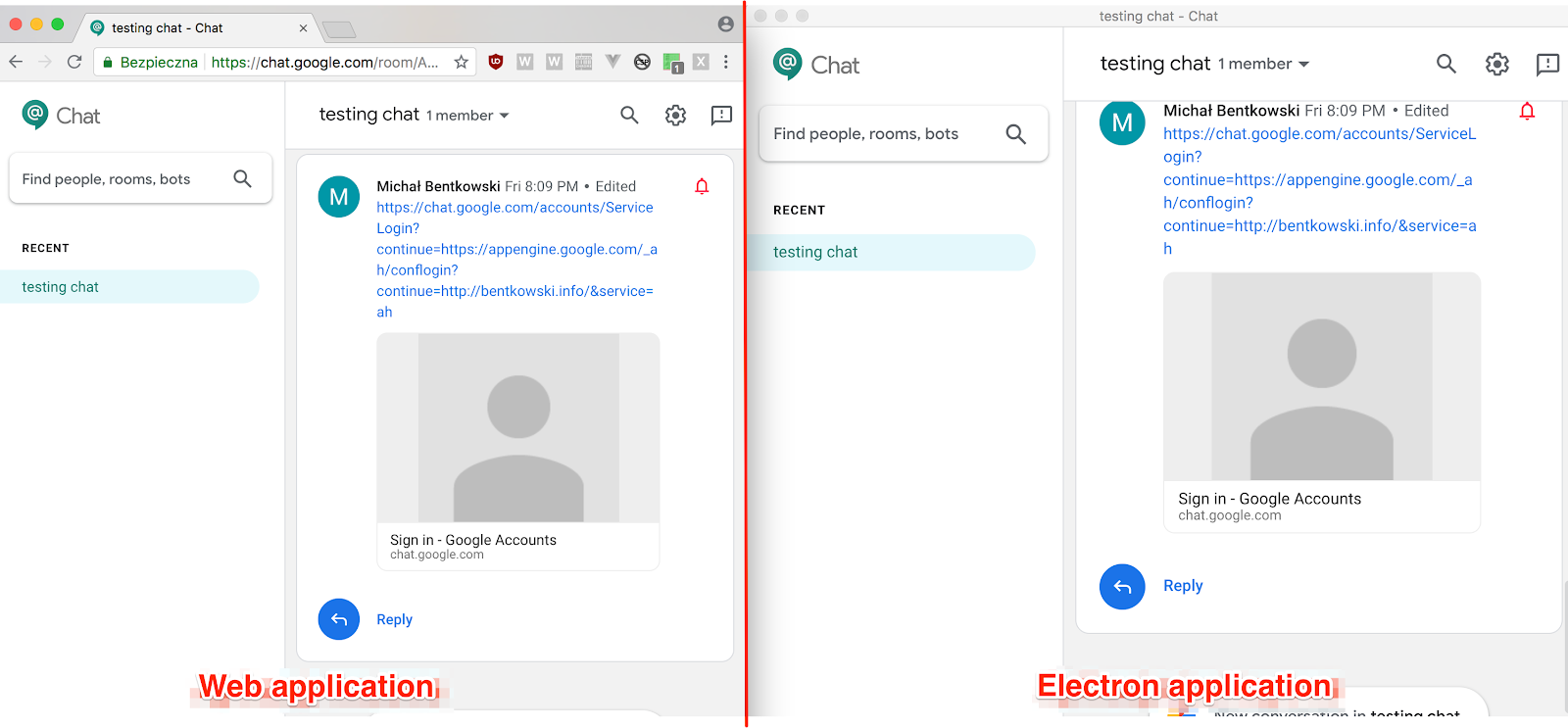
Security at events. Use the following filter selections to narrow your security events search by month. Perform a risk assessment. It is also important that purchasers review the insurance cover. You need to be sure that any security services that you buy in are complying with the law. Ensuring security at events is and should always be an essential part of any event planners thoughts when organising any size event. The types of security you need will depend on the size scope location and type of event you re planning. When reviewing security at events purchasers should consider various factors prior to their decision.
Are you planning an event. The bottom line is that events and venues can be vulnerable. This means ensuring that individuals are properly licensed where necessary. An injury to a guest. Whether it is a corporate meeting a party an entertainment venue a promotional event or anything else you have in the works event security always requires a rare breed of event security guards who can bring the blend of experience judgement sensitivity efficiency and professionalism that you expect and your guests deserve. Many companies offer event security however many do not have the relevant experience or operational capacity to perform the role. Here are 3 tips to take note of as you plan for your event to ensure a safe and secure function.
Poor event planning management crowd control security and ineffective emergency response increase the likelihood of injuries property damage and even catastrophic attacks. Wherever large crowds congregate can be tempting targets for terrorists or lone wolves with psychiatric problems. Security has always been an important component of event planning but the frequency of violent incidents at public venues in recent years has heightened awareness and concern. Even false alarms can send crowds into a panic. That s why you must plan your security strategy during the planning process. Security keeps you covered in case of. Use the following filter selections to narrow your security events search by region.
With the recent spate of terror attacks around the globe event security has now become what feels like a painful topic thrust under the spotlight for many event planners. It is very important that the organiser checks if the prospective company has appropriate insurance. Events such as trade shows and conferences are considered soft targets meaning they are relatively unprotected and vulnerable.